Complex Threats. Simple Response.
Hexnode XDR delivers the power of a SOC, unified in one platform.
Without XDR
Undetected Breach
Advanced malware evades signature-based Anti Virus, slipping through undetected.
Delayed Discovery
Teams spot breach post-damage, via ransom notes or outages, entry unclear.
Reactive patchwork
No visibility means only wipes or restores, while the actual vulnerability remains.
With
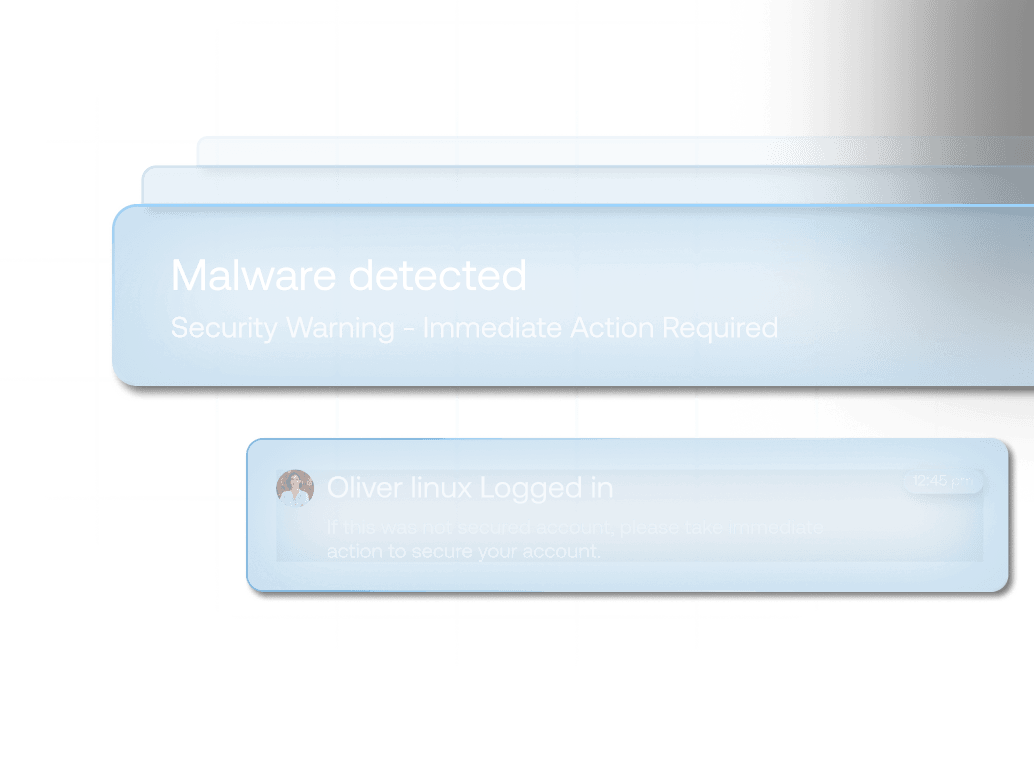
Contextualized Alerts
Alerts auto-enriched with endpoint data, giving instant threat context.
Automated Correlation
Hexnode XDR links signals across your endpoints, revealing attacks end-to-end.
Coordinated Response
Hexnode XDR triggers instant multi-layer defence: isolate, kill or quarantine endpoints and files.
Orchestrate Endpoint Security
From setup to response, Hexnode XDR gives full, intuitive security control.
The Modern XDR Toolkit
Total endpoint command: full visibility, decisive control, smart automation.
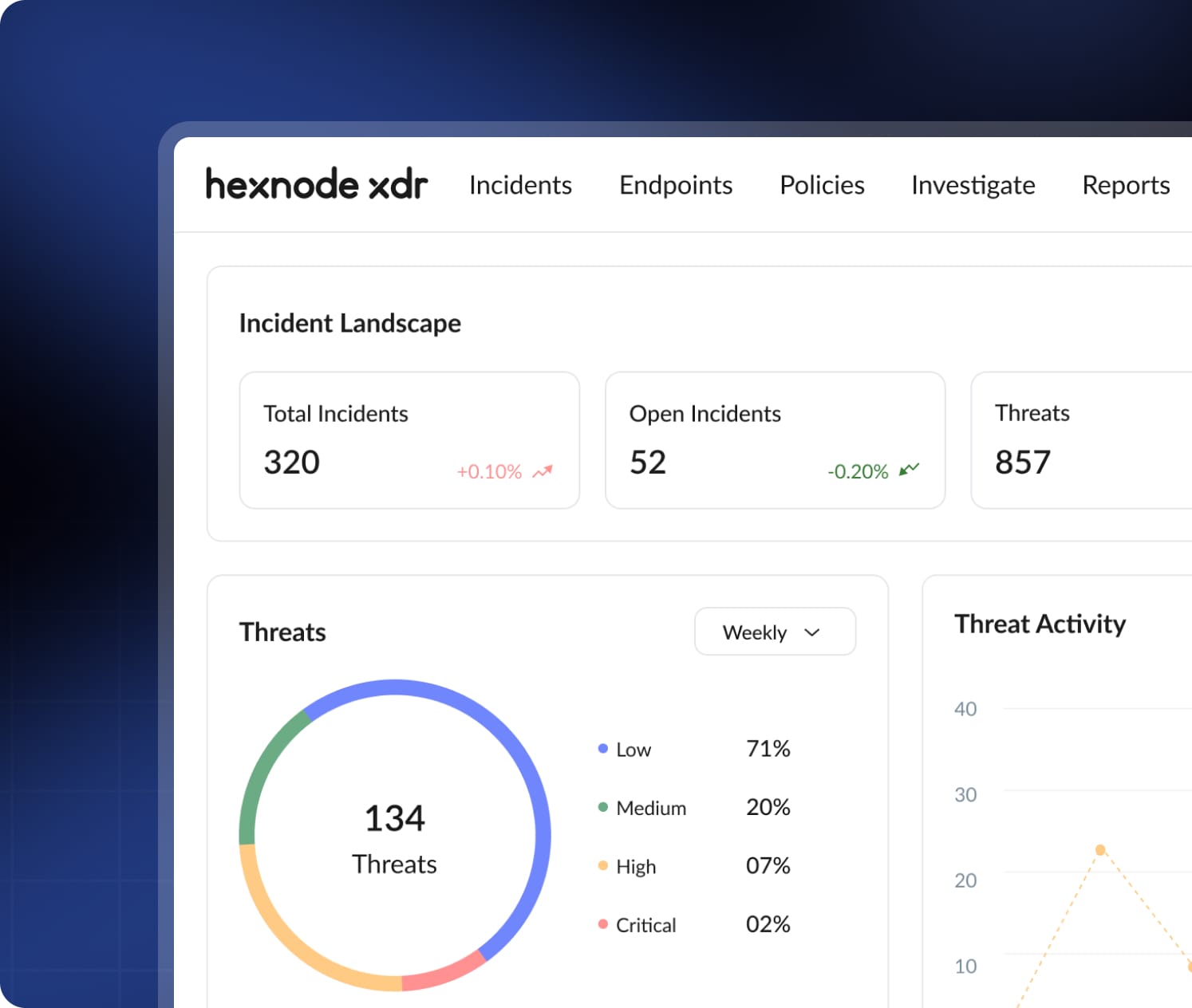
See Everything. Instantly.
See threats, patterns, and risks clearly with a single mission control.
See Everything. Instantly.
See threats, patterns, and risks clearly with a single mission control.
Unified Dashboard
Get a 360° real-time view of threats, active incidents, and endpoint health.
Threat Trends & Analytics
Threat trend visualisation to detect patterns and stop risks before they strike.
MITRE ATT&CK® Insights
Hexnode XDR maps threats to MITRE ATT&CK®, revealing motive and method.
Complete Device Vitals
Drill into any endpoint; see health, policies, and color-coded events.
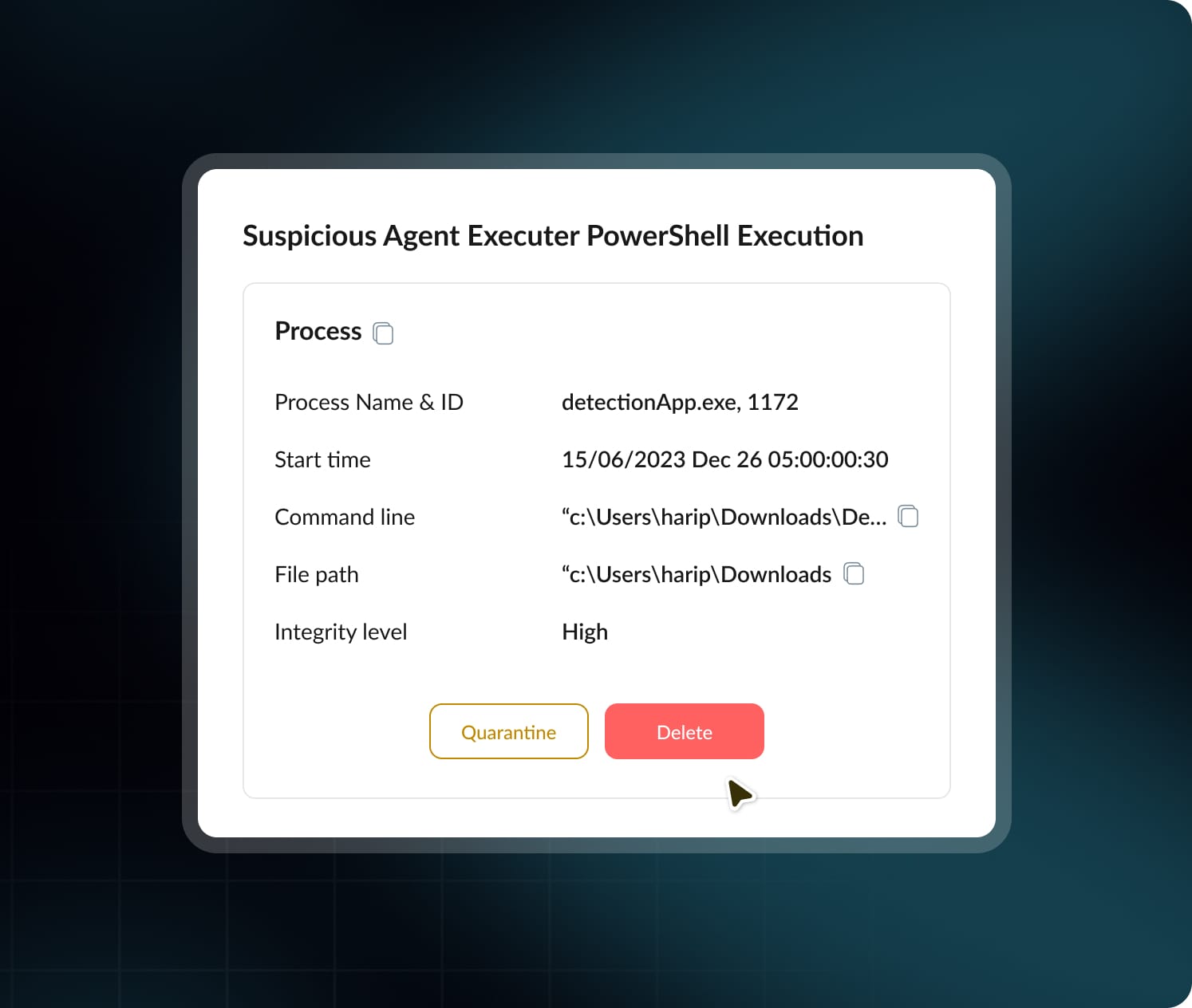
Respond with Speed and Certainty
Hexnode XDR empowers you to stop threats and contain breaches in one click.
Respond with Speed and Certainty
Hexnode XDR empowers you to stop threats and contain breaches in one click.
Isolate Device
One click cuts network access to devices, halts spread, and preserves control for forensics.
Kill Process
Kill malicious processes instantly on any endpoint with a single click.
Quarantine File
Safely contain malicious files, blocked, encrypted, and ready for review.
Deep Scan & Timely updates
Verify remediation with Deep scan for device health & other vital parameters.
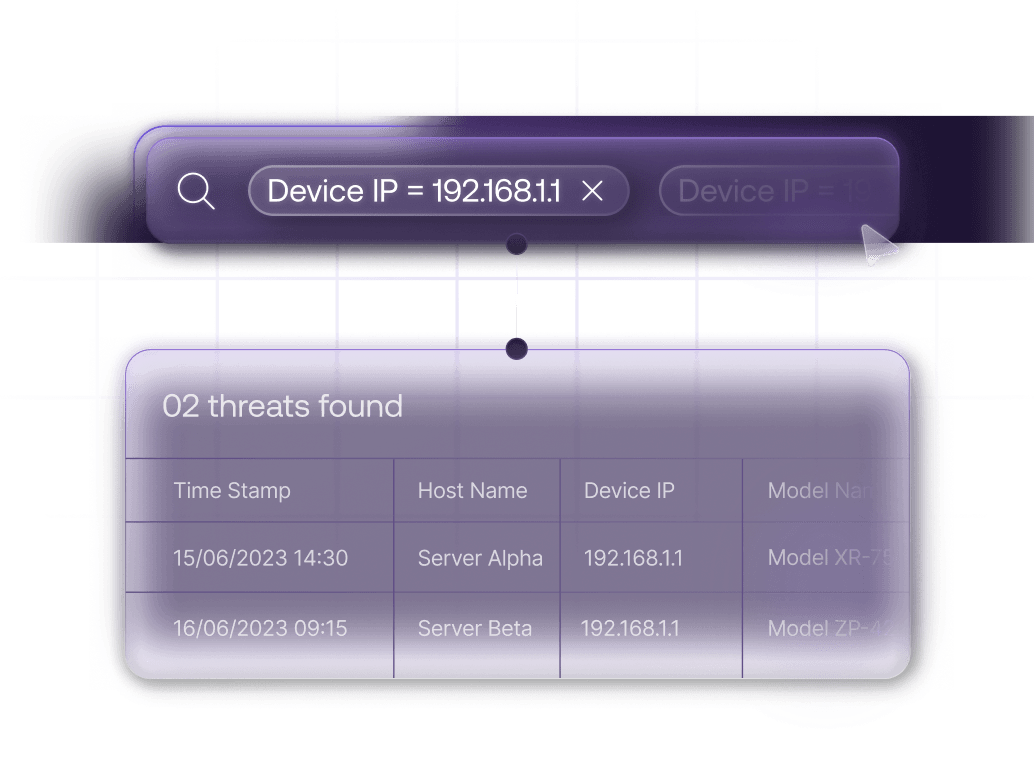
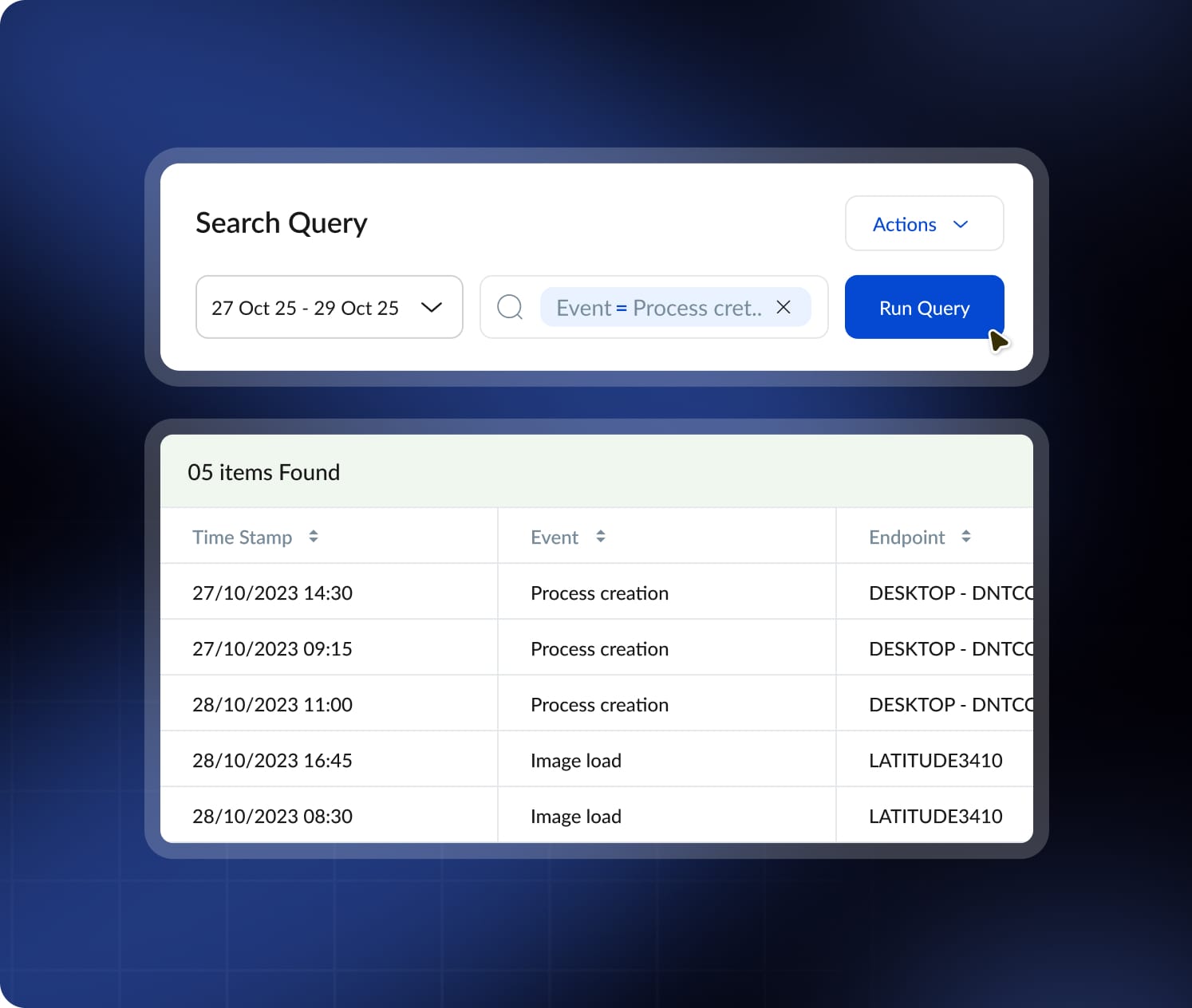
Threat Hunt with Precision
Proactively hunt for threats and understand the full story of an attack with a powerful, intuitive query engine.
Threat Hunt with Precision
Proactively hunt for threats and understand the full story of an attack with a powerful, intuitive query engine.
Intuitive Query Builder
Build complex queries with ease using search suggestions, recent history, and saved queries.
Advanced Investigation Query
Search 7 days of detailed endpoint data stored for instant access.
Efficient Query Workflow
Build, save, and share queries with a fast, intuitive interface.
Actionable Data Tables
View, filter, and export query results in a clean data table.
Put Your Security on Autopilot.
Enforce consistent, round-the-clock security with smart automated defense.

Put Your Security on Autopilot.
Enforce consistent, round-the-clock security with smart automated defense.
Smart Policy Lifecycle
Design, validate, and deploy robust security policies with ease.
Dynamic Endpoint Groups
Automate policy assignment with groups based on device criteria.
Custom Alert Profiles
Build fine-tuned alerts to eliminate noise and alert fatigue.
Seamless Agent Management
Keep agents updated and enable tamper protection automatically.
Resources worth exploring

14 day free trial
No credit card